Direct Access 2012 – Windows 7 Clients Tunneling Internally
On a recent installation I was tasked with setting up Direct Access on server 2012 for a client. The clients environment consisted purely of Windows 7 enterprise clients. The Direct Access server was in two NIC mode, one NIC in the DMZ and one sidestepped onto the LAN. After getting passed an issue where the DMZ NIC kept getting a domain profile, setting up certificate services for IPSEC I was ready to test client connectivity.
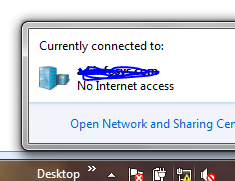
I put a laptop onto tethered 4g to emulate external access and the laptop connected to the Direct Access server successfully over IPHTTPS. As I was happy about the test being successful I connected the laptop again over Ethernet to the domain. When I did this I noticed that LAN NIC stated “no connection to the internet”.
I did a few tests;
- Pinged NLS.domain.com – No success
- Checked the clients DNS status with netsh dns show state.
- Checked the clients NRPT with the command netsh name show eff
- Checked the status of the clienst IPHTTPS with netsh int http show int
- Checked IPSEC mainmode with netsh advf mon show mmsa
From this I could work out that for some reason the Windows 7 client was trying to access to the domain via Direct Access while on the internal LAN.
The only way to get the machine to be able to see the domain was to disable Direct Access on the Windows client, this is done with the following command.
net stop "ip helper"
This command effectively disables IPV6 and the machine will the start to communicate with the domain again. Now that I had the Windows client back on the domain I had to find out why the machines thought they where external when in fact they where connected to the LAN. I eventually came across this not very well known issue with the Network Location Awareness service on Windows 7 not being able to identify its location when configured to configured to use Direct Access. Take a look at the link below and patch this clients that this fault effects, your clients will then be able to detect that they are LAN connected and will not attempt to tunnel.
Tags: directaccess;iphttps