
How To Enable SSL 3.0 Server 2008 /SBS 2008/SBS2011
Problem
Server 2008,server 2008 SBS and SBS 2011 do have the functionality for SSL 3.0 however by default it does not understand anything that tries to connect with this protocol. For security reasons if you need to enable SSL 3.0 on your server we can enable it with some additional registry keys. Follow the step by step guide below. (MAKE SURE THAT YOU BACKUP YOUR REGISTRY BEFORE APPLYING THOSE CHANGES)
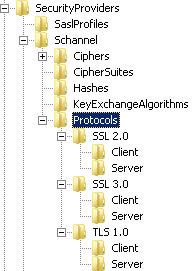
Use regedit to add the following keys ( right click on protocols -> new -> key -> “SSL 2.0” then “SSL 3.0” then “TLS 1.0” )
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0 HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0 HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0
Under each of the keys above you need to create additional keys “Client” and “Server”
For SSL 2.0:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server
For SSL 3.0:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server
For TLS 1.0:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server
Then you will have to create DWORD (32bit) value called “Enabled” under each “Client” and “Server” key for “SSL 2.0, SSL 3.0 and TLS 1.0”
Value name = Enabled
Value date = 0
Value date can be set to “1” – Enabled or “0” – Disabled
In my scenario the values were “enabled” (set to 1) for SSL 3.0 and TLS 1.0 and “disabled” (set to 0) for SSL 2.0
Here is a disabled value for ssl 2.0

Enable ssl 3.0 server 2008
and here is SSL 3.0 enabled
• Next step is to add correct Ciphers, to do so you will have to navigate to the following key in the registry
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Ciphers
• (right click on “Cliphers” New -> Key)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Ciphers\RC2 128/128 HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128 HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168/168
• That’s all! Now you need to restart your server to apply those changes.
• If you are using TMG 2010 or ISA 2006 to publish the website externally you will need to apply exactly the same settings to registry to it.
If you need to buy an SSL cert, check out GoDaddy and if you want to know how to install the certificate then follow this guide.







Dale Unroe
| #
Noticed in SBS 2011 that the only ~\SCHANNEL\Protocols key I’ve got is SSL 2.0\Client
A Compliance Scan by Security Metrics is pushing for use of SSL 3.0 and ceasing SSL 2.0. This guide is useful assuming it can be carried forward for use with SBS 2011 (Win2k8R2 underneath). Perhaps you could make a comment that it in fact is applicable to the current SBS 2011 system. …Thx Dale
Reply
Allen White
| #
Hi Dale, thanks for your input, Ive updated the article as it also covers SBS2011 ( effectively 2008 R2 ). I currently have a client who is having similar issues with securtiy metrics.. they are having that many issues they are think of using another compliance company.
Thanks
Al
Reply
Josh
| #
I am assuming that is a typo in the Ciphers key —
“HKEY_LOCAL_MACHINESYSTEM\CurrentControlSet\
Control\SecurityProviders\SCHANNEL\CiphersRC4 128/128”
Should read “HKEY_LOCAL_MACHINESYSTEM\CurrentControlSet\
Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128”?
Reply
Allen White
| #
Correct it is a typo, the CMS the website uses is having issues post BACKSLASHES, at the mo. Thanks, ive corrected
Reply
Sameer
| #
Hi Allen White .
I know it’s a long time since the time you wrote the article , but I ran into a nightmare and I guess this article would solve my problem , I have TMG 2010 sp2/r4 , I have external server need to do a mutual authentication with an internal web application certificates through TMG , so EXT TMGINT , I got this error on TMG :
{
An SSL 3.0 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The SSL connection request has failed
}
I saw the registry and I did not found SSL v.3 , if I follow the article , would it solve my problem ?
I get confused for the ciphers points , after I create the cipher key should I paste the 92RC4 128/128 in the key name ?
hope to reply to me
Reply
Ada Scott
| #
I know that you’re dealing with servers and networks, but I hope you read my comment and respond. My problem is with a stand-alone PC running Win 7 64-bit w/ IE 11 in BOTH 64- and 32-bit versions and lots of IE hangs & app crashes (almost all of them the 32-bit), and now Schannel Errors 36874 & 36888 up the wahzoo (sp?). The 1st error is “An SSL 3.0 connection request was received from a remote client application…” The 2d informs “fatal alert was generated: 40. The internal error state is 107.”
Advanced Internet Options has “Use SSL 3.0” & “Use TLS 1.0” enabled. Only those.
Yesterday evening I decided to install the MS updates that had been waiting for at least a week (while I took care of a strange Blue Screen event that left no entry in the Event Logs & no dumps, but did leave fallout). There were, of the announced 14 Essential updates listed, 29 installed for Office 2010 alone, and none for IE according to the Installed Updates List. The Reliability Monitor says there was an IE Security Update.
The install process created a restore point. I saw the message & progress bar.
I did a full shutdown/reboot. I used Word, then IE to email 2 documents. Went to the System Log & was bowled over by the Schannel errors. Decided to roll back the newly installed progs by doing a restore. There was not a single restore point. In the morning there had been 11 covering a 12-day period, and then there was the system-generated one. All gone.
So I’m stuck with the Schannel errors and the question of which protocols should be enabled–unless I want to uninstall each update individually, and I don’t.
Shall I activate SSL 2.0? Should I turn off SSL 3.0? Whichever I have, should I follow your logical and lucid instructions to create new registry keys and values? For TLS 1.0 and not for the SSLs? Can I get rid of the 32-bit IE? (I can’t help but feel that IE is somehow to blame.)
Desperately hoping for a reply. Thanks in advance.
Reply
Matt
| #
Ada, I’m dealing with the same issue. It’s only occurring on one computer on a network with 30 other computers. I completely wiped the drives, reinstalled OS and still have those two Schannel errors. I hope someone can help us with this.
Reply